Performance indicators for application analytics
You can view the performance indicators, along with its categories that occur in NetScaler web applications. To view these indicators, you must ensure to enable analytics andmetrics collectoron the ADC instance:
After you enable analytics and metrics collector, you can view the following indicators by navigating toApplications>Dashboard, selecting an application, and scrolling down toIssuessection:
Response time
This issue detects when the application response time to respond to client requests deviates from the configured threshold value. Click theResponse Timetab to view the issue details.
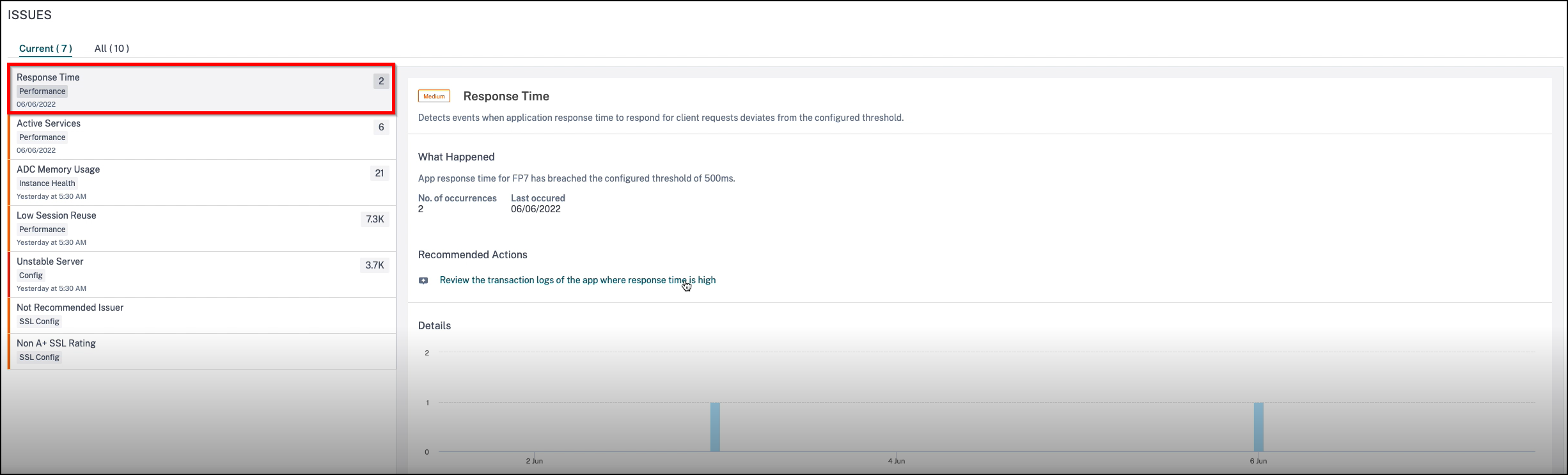
In theRecommended Actions, click to view theTransaction Logsthat show the application with > 500 ms response time.
UnderDetails, you can view:
The graph indicating the total events for the selected time. Click to apply filter and view details
When the issue has occurred
The total occurrences for the selected time
The issue severity such as low, medium, and high
The detection message indicating the total transaction response time exceeding the configured threshold value.
Active services
This issue detects when the % of active services bound to the virtual server is lesser than the configured threshold value. Click theActive Servicestab to view the issue details.

In theRecommended Actions, click to view details of the services bound to the virtual server.
UnderDetails, you can view:
The graph indicating the total events for the selected time duration. Click to apply filter and view details
When the issue has occurred
The total occurrences for the selected time duration
The issue severity such as low, medium, and high
The detection message indicating the % of active service sessions and the configured threshold value.
Average CPU usage
This issue detects when the ADC CPU usage for this application exceeds the configured threshold value. Click theAverage CPU Usagetab to view the issue details.
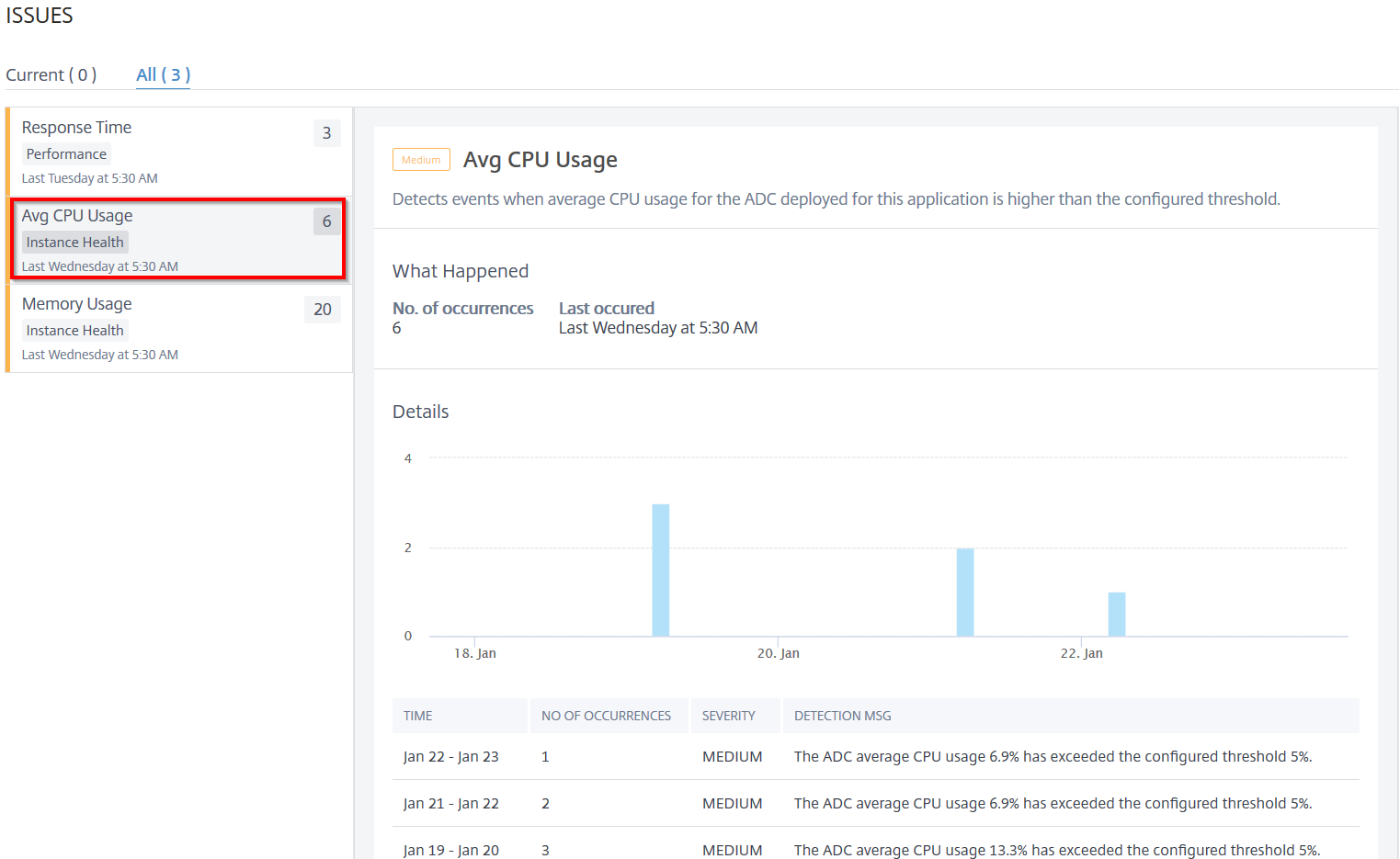
UnderDetails, you can view:
The graph indicating the total events for the selected time duration. Click to apply filter and view details
When the issue has occurred
The total occurrences for the selected time duration
The issue severity such as low, medium, and high
The detection message indicating the ADC average CPU usage % and the configured threshold value.
Average application CPU usage
This issue detects when the application CPU usage exceeds the configured threshold value. Click theApp CPU Usagetab to view the issue details.
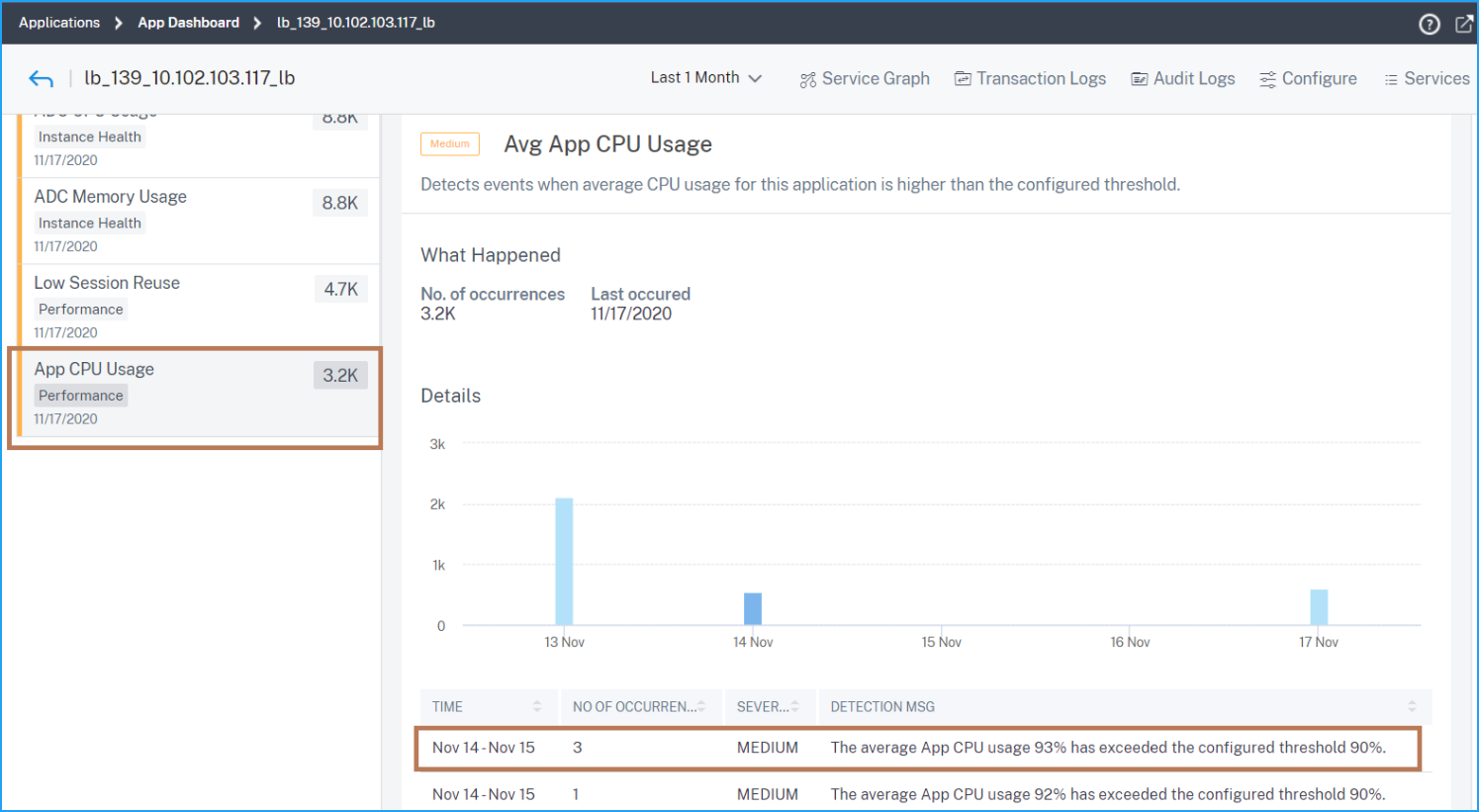
UnderDetails, you can view:
The graph indicating the total events for the selected time duration. Click to apply filter and view details
When the issue has occurred
The total occurrences for the selected time duration
The issue severity such as low, medium, and high
The detection message indicating the application average CPU usage % and the configured threshold value
Memory usage
This issue detects when the ADC memory usage for this application exceeds the configured threshold value. Click theMemory Usagetab to view the issue details.
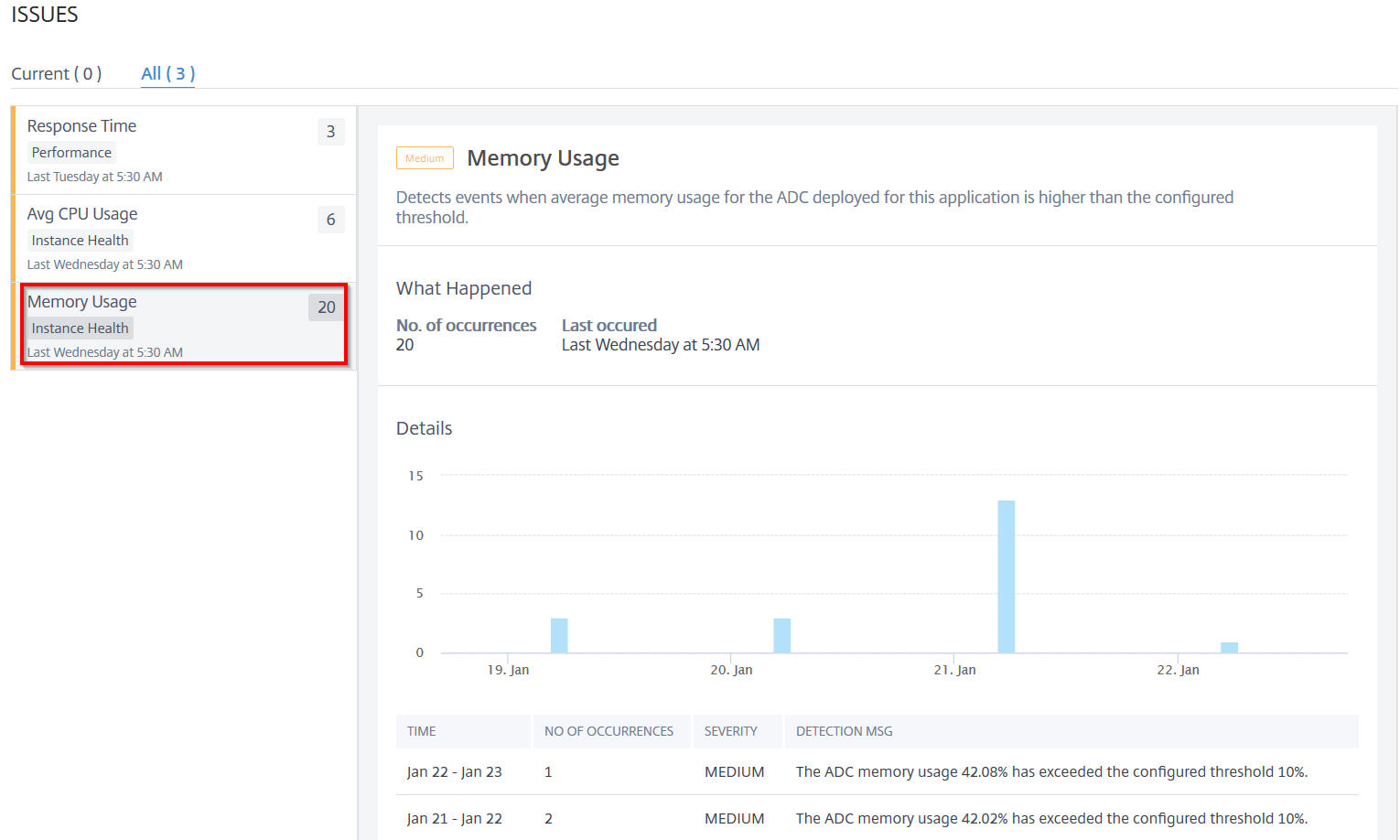
UnderDetails, you can view:
The graph indicating the total events for the selected time duration. Click to apply filter and view details
When the issue has occurred
The total occurrences for the selected time duration
The issue severity such as low, medium, and high
检测消息说明ADC平均memory usage % and the configured threshold value.
NIC discards
A packet discard can happen when:
A received packet has some format errors
A receiving device does not have enough storage for the packets
Using theNIC Discardsindicator, you can view total packets discarded from the NIC. Click theNIC Discardstab to view the details.
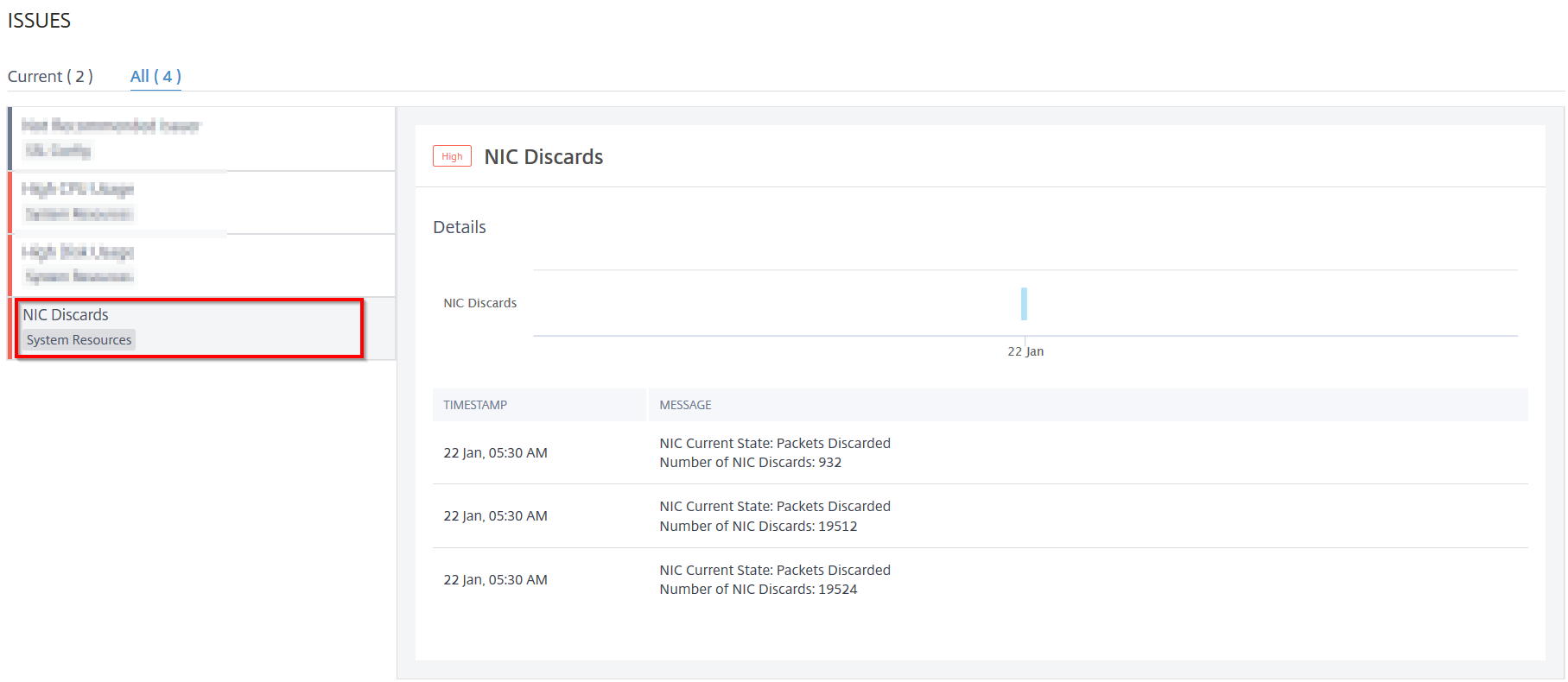
UnderDetails, you can view:
The time that occurred the anomaly
The message indicating the total packets discarded from NIC
Service flaps
As a network administrator, you must ensure for optimal availability of the application. When there are any network issues or configuration issues, the status and availability of an application server might impact the overall performance.
Using the service flaps events, you can identify the application that has issues. Service flaps events also help you:
Understand which service is in DOWN status for a specific duration
Understand how many services are in UP or DOWN state for a specific duration
Click theService Flapstab to view the service flaps details.
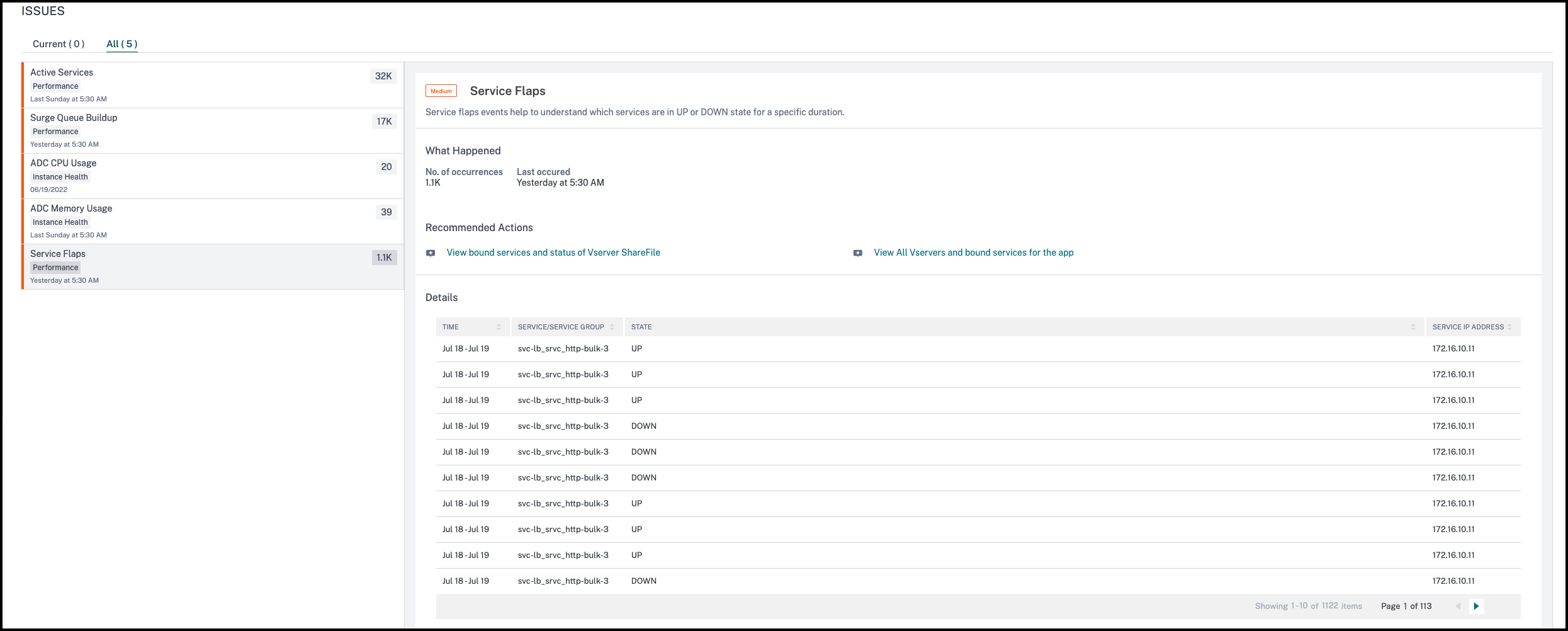
In theRecommended Actions, click to view the details of services that are bound to the virtual server.
You can view details such as number of occurrences and the time of last occurrence.
UnderDetails, you can view:
The time that occurred the service flap anomaly
The service/service group name
The service IP address
The current service status
Low session reuse
NetScaler instances process SSL transactions by offloading SSL handshake process from the server. Upon receiving the response from the server, the NetScaler instance completes the secure transaction with the client. Using the cached session parameters, NetScaler instance completes the SSL handshake process for the consecutive requests.
If in case these sessions are not reused, they become an overhead for the NetScaler instances. Using theLow Session Reuse指标,你可以identify if the actual number of sessions being reused is less.
Click theLow Session Reusetab to view the issue details.
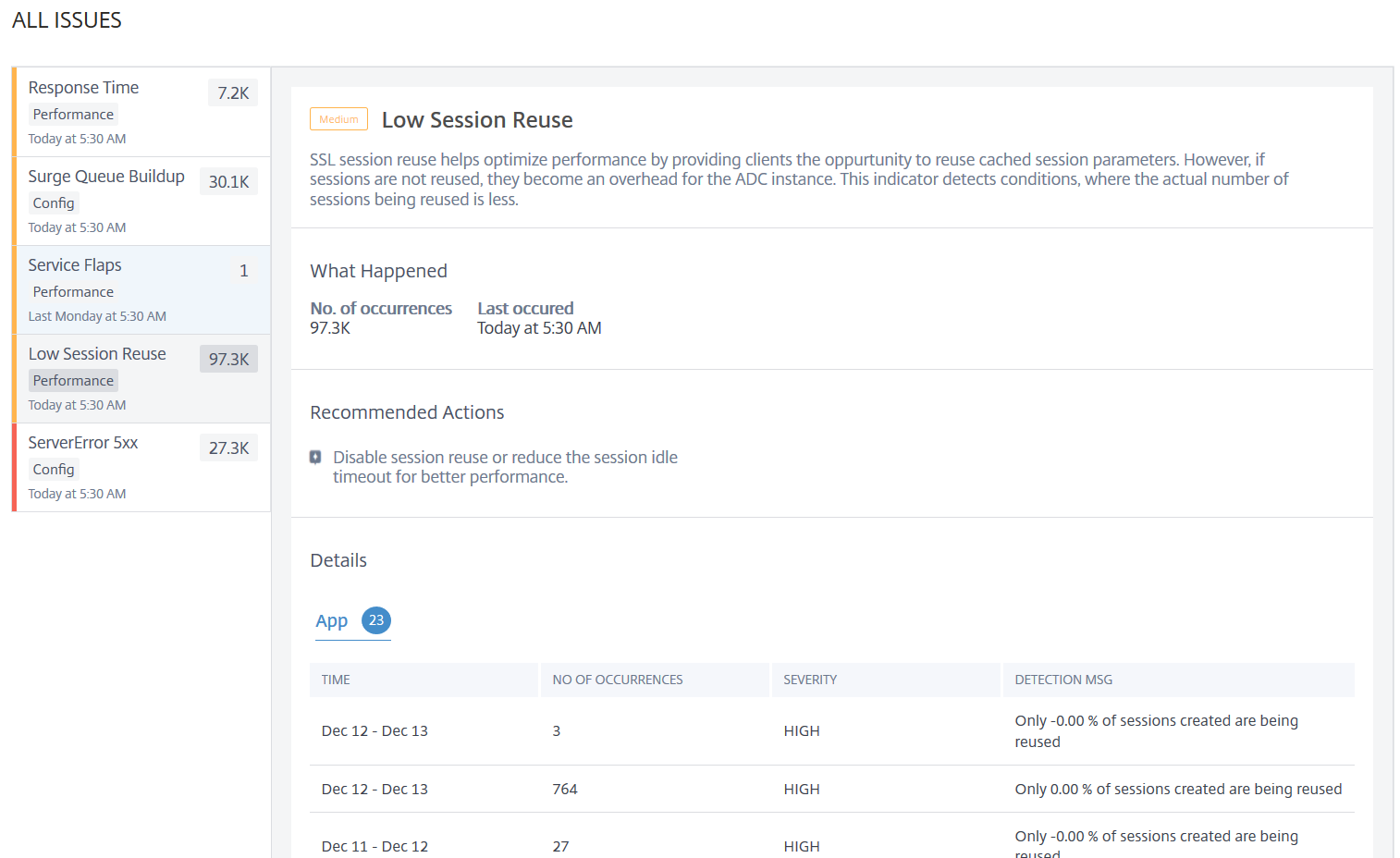
TheRecommended Action解决这个问题是禁用的session reuse or reduce the session timeout. For more information, seeSession Reuse.
UnderDetails, you can view:
Total applications that have Low session reusage
The time that occurred the low session reuse anomaly
Total occurrences
The anomaly severity such as high, low, and medium
The detection message indicating only % of the configured sessions are being reused
Improper persistence type
You must configure persistence on a virtual server if you want to maintain the states of connections on the servers represented by that virtual server (for example, connections used in e-commerce). The appliance then uses the configured load balancing method for the initial selection of a server, but forwards to that same server all subsequent requests from the same client.
Persistence is effective when existing sessions are reused to serve subsequent requests. If persistence session reuse is low, sessions created on ADC are just an overhead.
Using theImproper Persistence Typeindicator, you can determine if the persistence usage on a virtual server is low. Click theImproper Persistence Typetab to view the issue details.
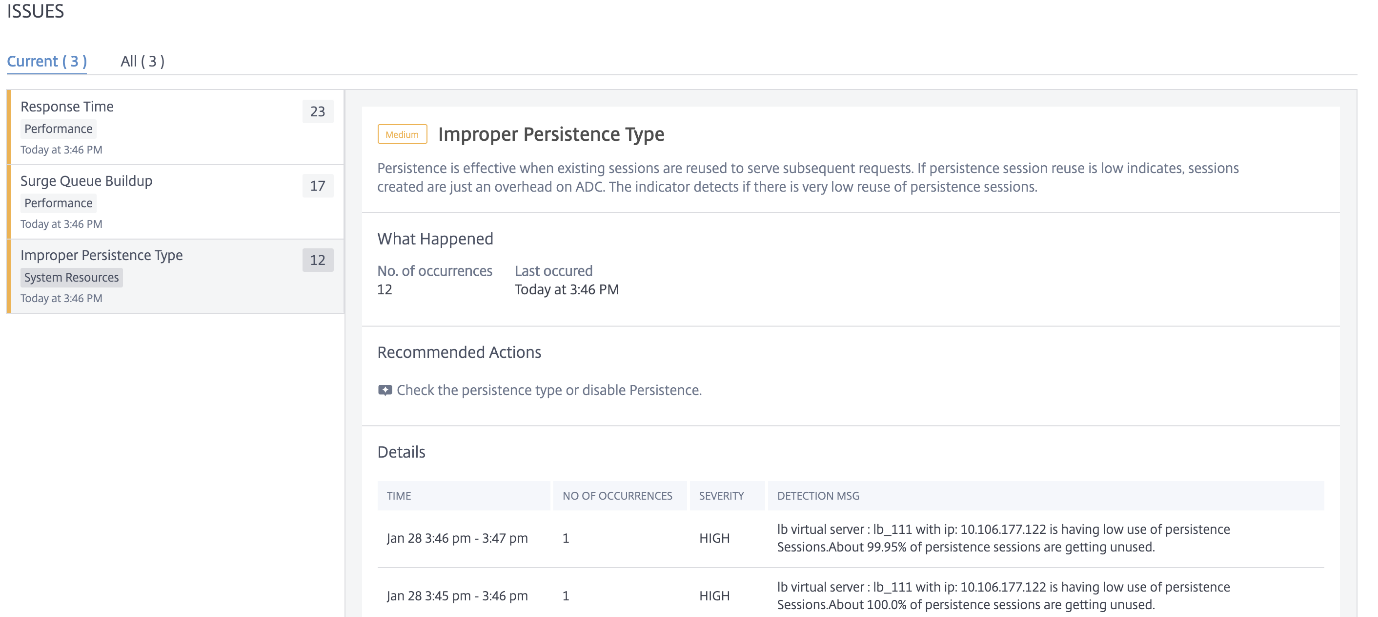
TheRecommended Actionto troubleshoot the issue is to check the persistence type or disable persistence. For more information, seePersistence Settings.
UnderDetails, you can view:
The time that occurred the anomaly
Total occurrences
The anomaly severity such as high, low, and medium
The detection message indicating the % of sessions that are unused
Unstable Server
In some scenarios, the web server responds with status codes when it is unable to handle the requests for reasons such as invalid requests, temporary overloading, or server maintenance. These errors are displayed with error codes, which define various scenarios of the errors. For example,
502 Bad GatewayThe server is acting as a gateway or proxy and received an invalid response from the upstream server.
503 Service UnavailableThe server is unavailable. The servers might be overloaded or down for maintenance.
504 Gateway Time-outThe server is acting as a gateway or proxy and did not receive a timely response from the upstream server.
These can be temporary conditions, but sometimes you have to implement a corrective measure on the webservers to make the webpages up and available.
Using theUnstable Serverindicator, you can view these failures and take decisions about corrective actions to overcome the issues and ensure the client requests are served and the webpages are always available.
Select theUnstable servertab to view the issue details.
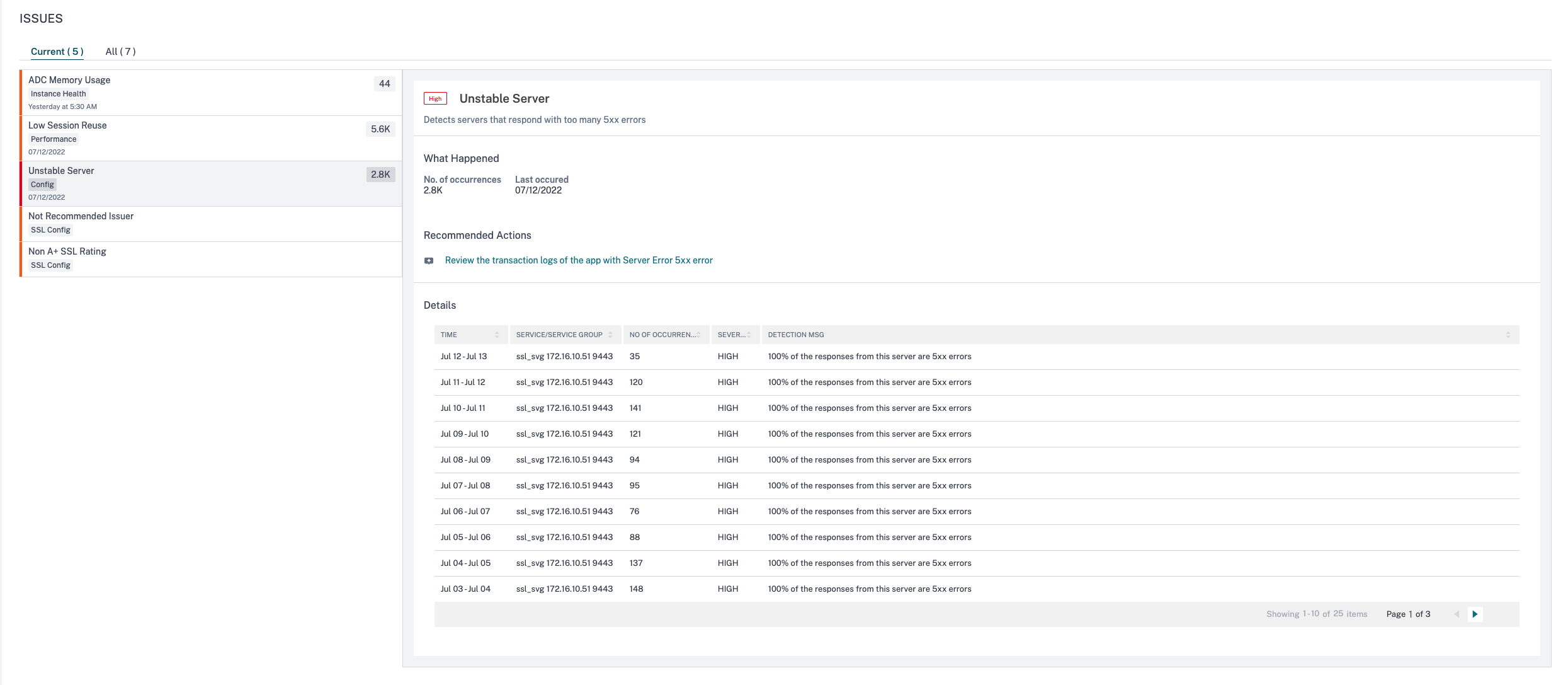
In theRecommended Actions, click to view theTransaction Logsthat show the application with Response code 5xx error.
You can also try the following troubleshooting methods:
Configure L7 monitors with appropriate parameters for the server that responds with 5xx errors. A monitor is an entity that tracks the service health. The appliance periodically probes the servers using the monitor bound to each service. If a server does not respond within a specified response timeout, and the specified probes fail, the service is marked DOWN. The appliance then performs load balancing among the remaining services. For more information to configure a monitor, seeCustom Monitors
Troubleshoot the server
UnderDetails, you can view:
The time that occurred the unstable server anomaly
The service/service group name
Total occurrences
The anomaly severity such as high, low, and medium
The detection message indicating % of the responses from this service reporting 5xx errors
For detailed information on server error web transaction, seeWeb transaction analytics for server errors
SSL Real Time Traffic
In NetScaler instance, you can use an SSL profile for processing SSL traffic. The SSL profile comprises certain SSL parameters for virtual servers, services, and service groups. TheSSL Real Time Trafficindicator analyzes the SSL traffic to identify real time traffic and suggests optimal configuration settings for improving latency.
Click theSSL Real Time Traffictab to view the issue details.
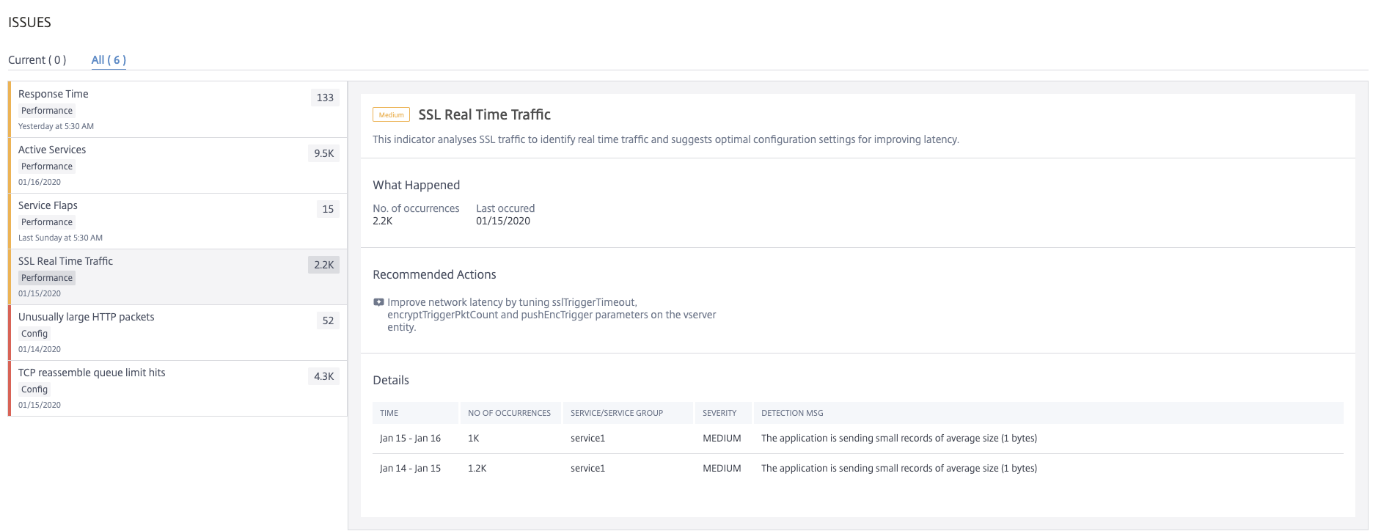
TheRecommended Actionto troubleshoot the issue is to improve the network latency by updating SSL parameters. For more information, seeGlobal SSL Parameters.
UnderDetails, you can view:
The time that occurred the anomaly
The service/service group name
The anomaly severity such as low, medium, and high
The detection message with the current setting on the application
Unusually Large HTTP packets
An HTTP transaction uses request-response messages between the client and the server. In the request and response messages, HTTP headers are the values that are displayed in the HTTP protocol. You can configure the HTTP header length in virtual server, service, or service group to avoid 4xx errors.
When an HTTP request/response exceeds the maximum header length, it can be a possible attack. Using theUnusually large HTTP packetsindicator, you can view the occurrences where the HTTP messages with HTTP header size exceed the configured values.
Click theUnusually large HTTP packetstab to view the issue details.
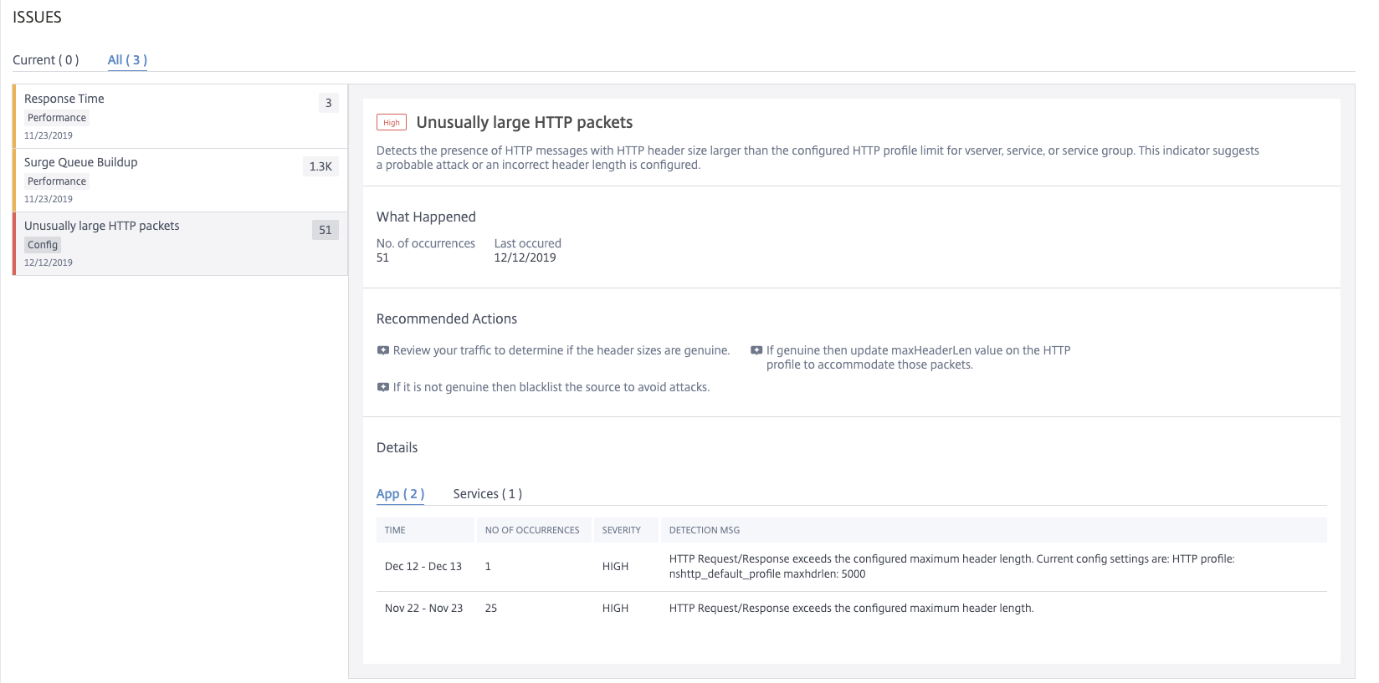
TheRecommended Actionsto troubleshoot the issue are:
Review the traffic to determine the header size is genuine. If the header size is genuine, then update the header value on the HTTP profile. For more information, seeBuffer Overflow Check.
If the header size is not genuine, add the source to the block list to avoid attacks.
UnderDetails, you can view:
The time that occurred the anomaly
Total occurrences
The anomaly severity such as high, low, and medium
The detection message indicating the current HTTP header length configured on the virtual server, server, or service group
TCP reassembly queue limit hits
TCP maintains an Out-of-Order queue to keep the OOO packets in the TCP communication. This setting impacts NetScaler memory if the queue size is long as the packets need to be kept in runtime memory.
This needs to be kept at an optimized level based on the kind of network and application characteristics.
Using theTCP reassemble queue limit hitsindicator, you can view if the Out-of-Order packets on a TCP connection exceed the configured out of order packet queue size.
Click theTCP reassemble queue limit hitstab to view the issue details.
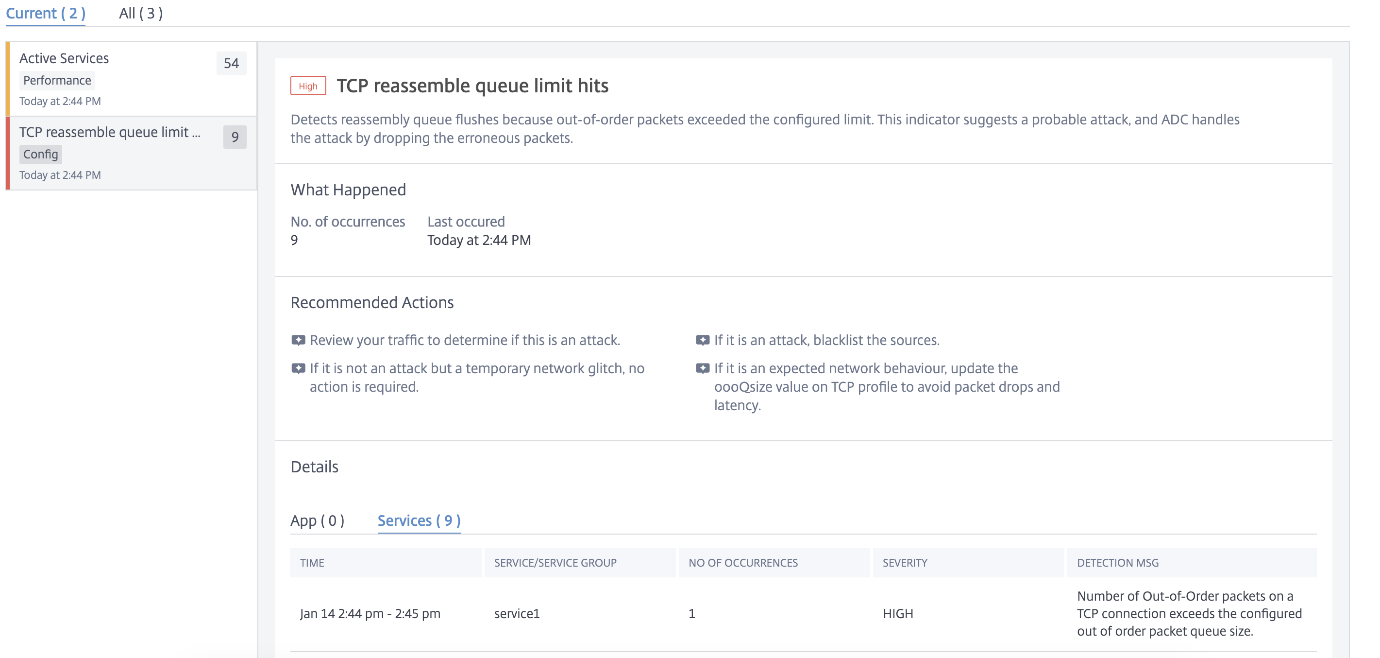
TheRecommended Actionsto troubleshoot the issue are:
Review the traffic and add the source to block list if it is an attack
If this is an expected network behavior, then update the out-of-order packets size value on TCP profile. For more information, seeTCP Optimization
If it is just a temporary network glitch, then no further action is required
UnderDetails, you can view:
The time that occurred the anomaly
Total occurrences
The anomaly severity such as low, medium, and high
The detection message indicating the current TCP profile and oooQsize settings
Surge Queue Buildup
When a server receives a surge of requests, the server becomes slow to respond to the clients. Often, the overload also causes clients to receive error pages. A virtual server needs to have enough back end servers configured to handle the incoming requests.
Using theSurge Queue Buildupindicator, you can view the virtual servers that have surge queue buildup. Click theSurge Queue Builduptab to view the issue details.
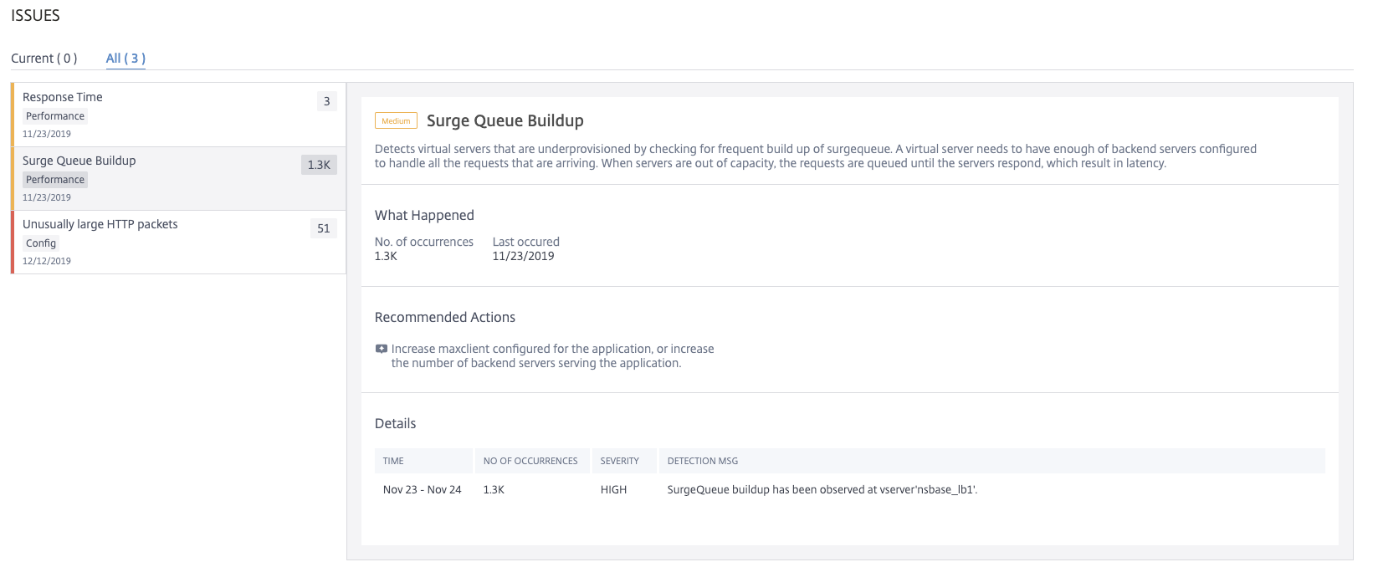
TheRecommended Actionsto troubleshoot the issue are:
Increase the number of client connections limit. For more information, seeSet a limit on the number of client connections
Increase the back-end servers to serve the application requests
UnderDetails, you can view:
The time that occurred the surge queue buildup anomaly
Total occurrences
The anomaly severity such as high, low, and medium
The detection message indicating the surge queue buildup on the virtual server
SSL rating
When an application is not having an A+ SSL rating, the app score gets impacted. Using theNon A+ SSL Ratingindicator, you can analyze the reasons for the application not having an A+ SSL rating. Click theNon A+ SSL Ratingtab to view the issue details.

TheRecommended Actionto troubleshoot the issue is to upgrade it to A+ SSL rating. For more information, seeUpgrade to A+ SSL Rating.
UnderDetails, you can view the issue details such as issue category, issue, and recommendation.
