Getting Started with Citrix ADC
Deploy a Citrix ADC VPX instance
Optimize Citrix ADC VPX performance on VMware ESX, Linux KVM, and Citrix Hypervisors
Apply Citrix ADC VPX configurations at the first boot of the Citrix ADC appliance in cloud
安装a Citrix ADC VPX instance on Linux-KVM platform
Prerequisites for Installing Citrix ADC VPX Virtual Appliances on Linux-KVM Platform
Provisioning the Citrix ADC Virtual Appliance by using OpenStack
Provisioning the Citrix ADC Virtual Appliance by using the Virtual Machine Manager
Configuring Citrix ADC Virtual Appliances to Use SR-IOV Network Interface
Configuring Citrix ADC Virtual Appliances to use PCI Passthrough Network Interface
Provisioning the Citrix ADC Virtual Appliance by using the virsh Program
Provisioning the Citrix ADC Virtual Appliance with SR-IOV, on OpenStack
Configuring a Citrix ADC VPX Instance on KVM to Use OVS DPDK-Based Host Interfaces
Deploy a Citrix ADC VPX instance on AWS
Deploy a VPX high-availability pair with elastic IP addresses across different AWS zones
Deploy a VPX high-availability pair with private IP addresses across different AWS zones
Configure a Citrix ADC VPX instance to use SR-IOV network interface
Configure a Citrix ADC VPX instance to use Enhanced Networking with AWS ENA
Deploy a Citrix ADC VPX instance on Microsoft Azure
Network architecture for Citrix ADC VPX instances on Microsoft Azure
Configure multiple IP addresses for a Citrix ADC VPX standalone instance
Configure a high-availability setup with multiple IP addresses and NICs
Configure a high-availability setup with multiple IP addresses and NICs by using PowerShell commands
Configure HA-INC nodes by using the Citrix high availability template with Azure ILB
Configure a high-availability setup with Azure external and internal load balancers simultaneously
Configure address pools (IIP) for a Citrix Gateway appliance
Upgrade and downgrade a Citrix ADC appliance
Authentication, authorization, and auditing application traffic
Basic components of authentication, authorization, and auditing configuration
On-premises Citrix Gateway as an identity provider to Citrix Cloud
Authentication, authorization, and auditing configuration for commonly used protocols
Troubleshoot authentication and authorization related issues
-
-
-
-
-
-
Persistence and persistent connections
Advanced load balancing settings
Gradually stepping up the load on a new service with virtual server–level slow start
Protect applications on protected servers against traffic surges
Retrieve location details from user IP address using geolocation database
Use source IP address of the client when connecting to the server
Use client source IP address for backend communication in a v4-v6 load balancing configuration
Set a limit on number of requests per connection to the server
Configure automatic state transition based on percentage health of bound services
Use case 2: Configure rule based persistence based on a name-value pair in a TCP byte stream
Use case 3: Configure load balancing in direct server return mode
Use case 6: Configure load balancing in DSR mode for IPv6 networks by using the TOS field
Use case 7: Configure load balancing in DSR mode by using IP Over IP
Use case 10: Load balancing of intrusion detection system servers
Use case 11: Isolating network traffic using listen policies
Use case 12: Configure Citrix Virtual Desktops for load balancing
Use case 13: Configure Citrix Virtual Apps for load balancing
Use case 14: ShareFile wizard for load balancing Citrix ShareFile
Use case 15: Configure layer 4 load balancing on the Citrix ADC appliance
-
-
-
Authentication and authorization for System Users
-
Configuring a CloudBridge Connector Tunnel between two Datacenters
Configuring CloudBridge Connector between Datacenter and AWS Cloud
配置一个CloudBridge连接器之间的隧道a Citrix ADC Appliance and Virtual Private Gateway on AWS
Configuring CloudBridge Connector Tunnel between Datacenter and SoftLayer Enterprise Cloud
配置一个CloudBridge连接器之间的隧道a Citrix ADC Appliance and Cisco IOS Device
配置一个CloudBridge连接器之间的隧道a Citrix ADC Appliance and Fortinet FortiGate Appliance
CloudBridge Connector Tunnel Diagnostics and Troubleshooting
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde.(Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique.(Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica.(Aviso legal)
此内容已经过机器动态翻译。放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다.책임 부인
Este texto foi traduzido automaticamente.(Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt.(Haftungsausschluss)
Ce article a été traduit automatiquement.(Clause de non responsabilité)
Este artículo ha sido traducido automáticamente.(Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Configure HA-INC nodes by using the Citrix high availability template with Azure ILB
You can quickly and efficiently deploy a pair of VPX instances in HA-INC mode by using the standard template for intranet applications. The Azure internal load balancer (ILB) uses an internal or private IP address for the front end as shown in Figure 1. The template creates two nodes, with three subnets and six NICs. The subnets are for management, client, and server-side traffic with each subnet belonging to a different NIC on each device.
Figure 1: Citrix ADC HA pair for clients in an internal network
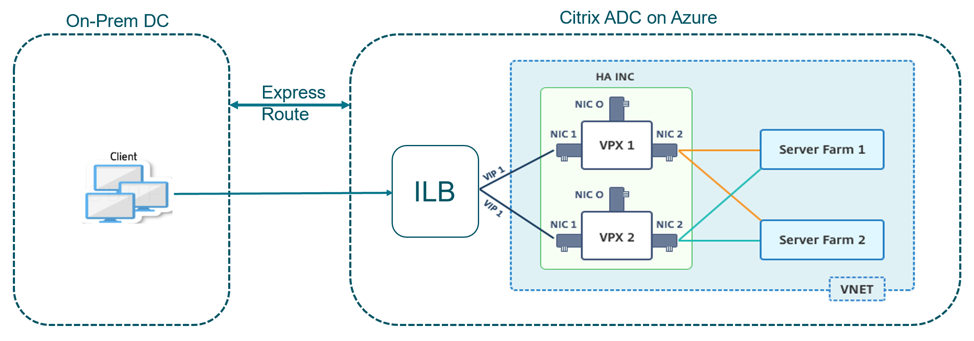
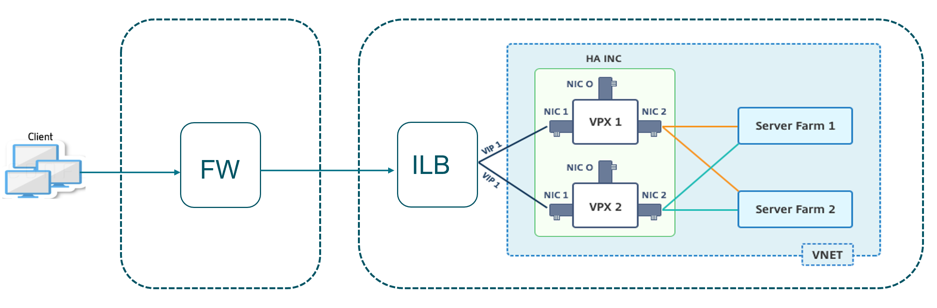
You can also use this deployment when the Citrix ADC HA pair is behind a firewall as shown in Figure 2. The public IP address belongs to the firewall and is NAT’d to the front-end IP address of the ILB.
Figure 2: Citrix ADC HA pair with firewall having public IP address
You can get the Citrix ADC HA pair template for intranet applications at theAzure portal.
Complete the following steps to launch the template and deploy a high availability VPX pair by using Azure Availability Sets.
From the Azure portal, navigate to theCustom deploymentpage.
TheBasicspage appears. Create a Resource Group. Under theParameterstab, enter details for the Region, Admin user name, Admin Password, license type (
VM sku), and other fields.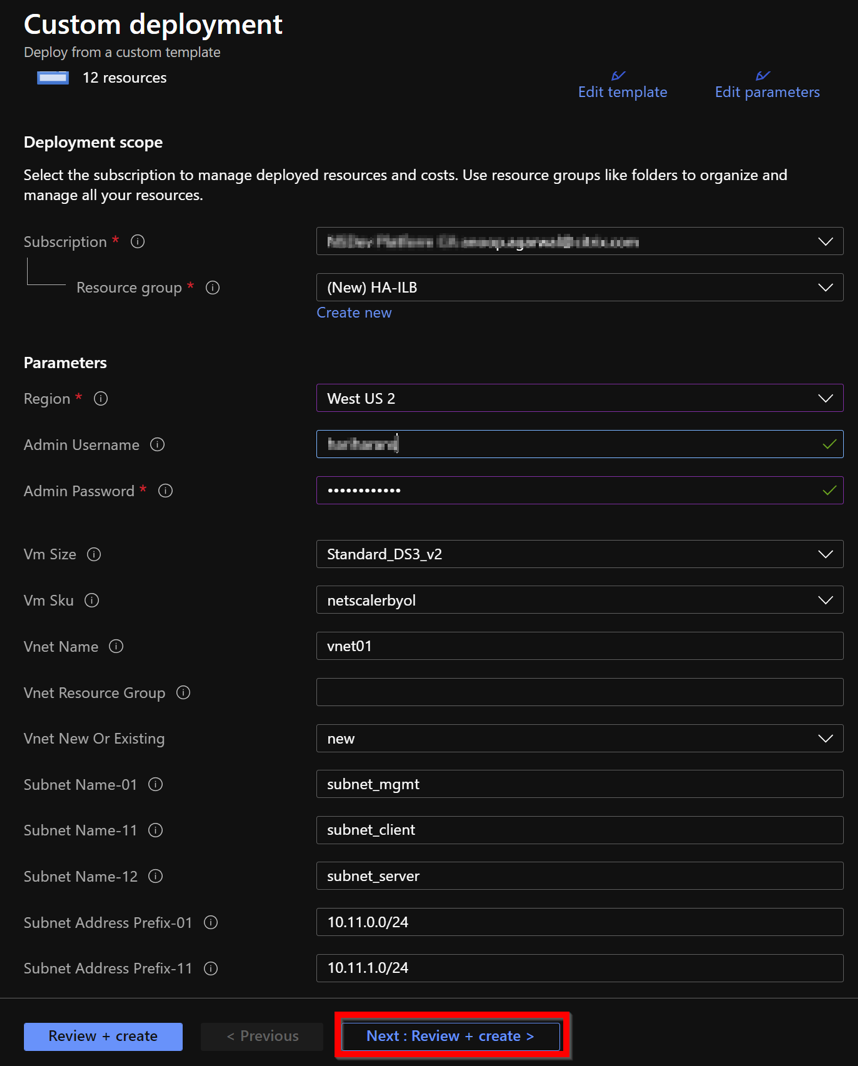
ClickNext : Review + create >.
It might take a moment for the Azure Resource Group to be created with the required configurations. After completion, select the Resource Group in the Azure portal to see the configuration details, such as LB rules, back-end pools, health probes. The high availability pair appears as ADC-VPX-0 and ADC-VPX-1.
如果需要进一步的修改你的哈setup, such as creating more security rules and ports, you can do that from the Azure portal.
Once the required configuration is complete, the following resources are created.
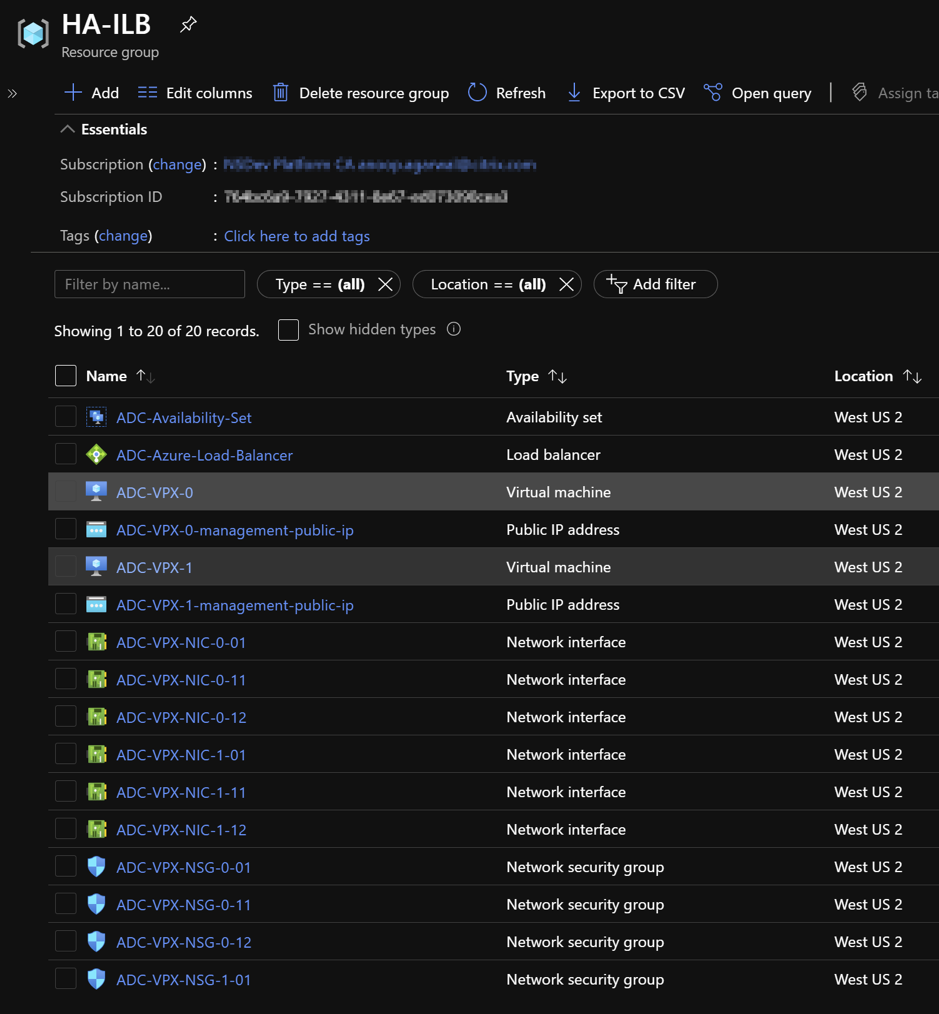
You must log on toADC-VPX-0andADC-VPX-1nodes to validate the following configuration:
- NSIP addresses for both nodes must be in the management subnet.
- On the primary (ADC-VPX-0) and secondary (ADC-VPX-1) nodes, you must see two SNIP addresses. One SNIP (client subnet) is used for responding to ILB probes and the other SNIP (server subnet) is used for back-end server communication.
Note
In the HA-INC mode, the SNIP address of the ADC-VPX-0 and ADC-VPX-1 VMs are different while in the same subnet, unlike with the classic on-premises ADC HA deployment where both are the same. To support deployments when the VPX pair SNIP is in different subnets, or anytime the VIP is not in the same subnet as a SNIP, you must either enable Mac-Based Forwarding (MBF), or add a static host route for each VIP to each VPX node.
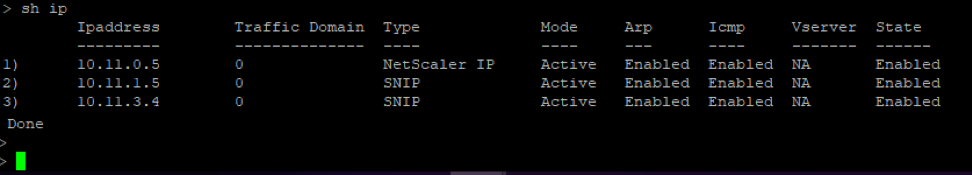
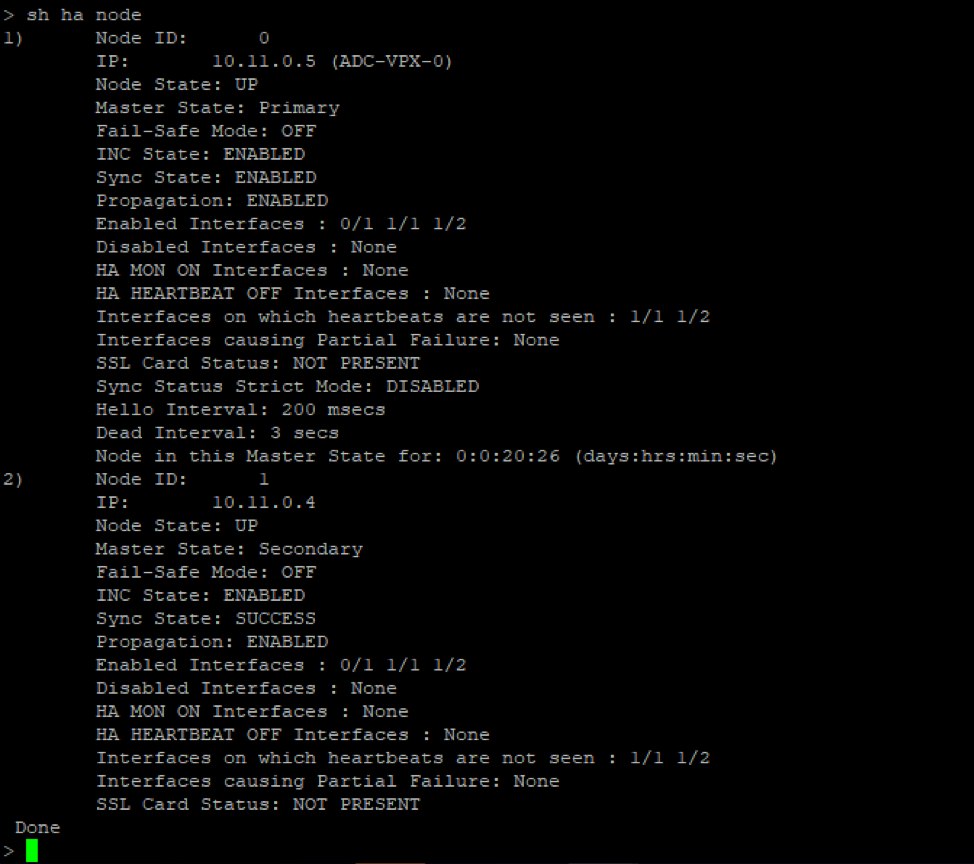
On the primary node (ADC-VPX-0)
On the secondary node (ADC-VPX-1)
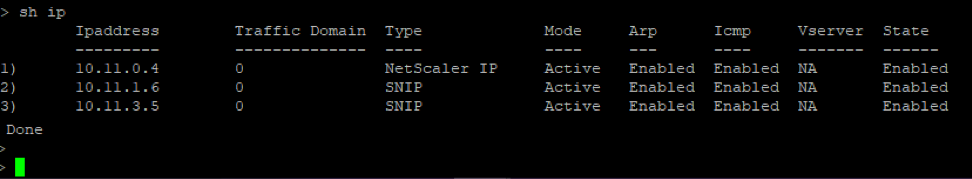
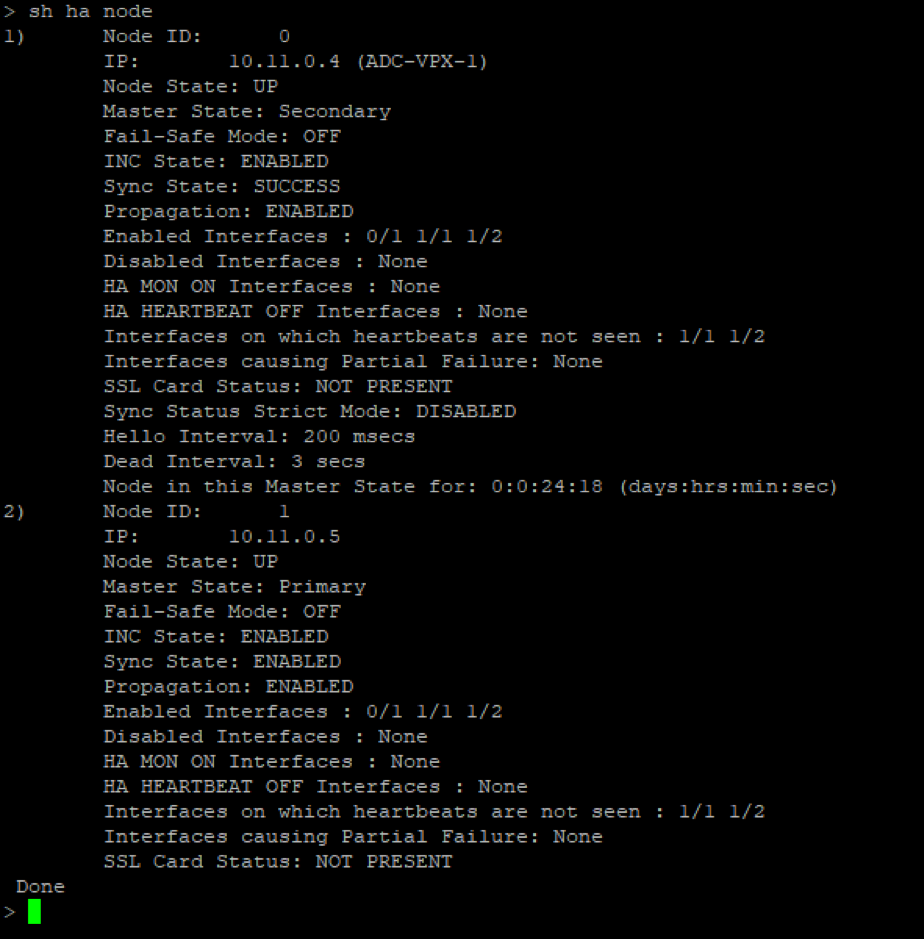
After the primary and secondary nodes are UP and the Synchronization status isSUCCESS, you must configure the load balancing virtual server or the gateway virtual server on the primary node (ADC-VPX-0) with the private floating IP (FIP) address of the ADC Azure load balancer. For more information, see theSample configurationsection.
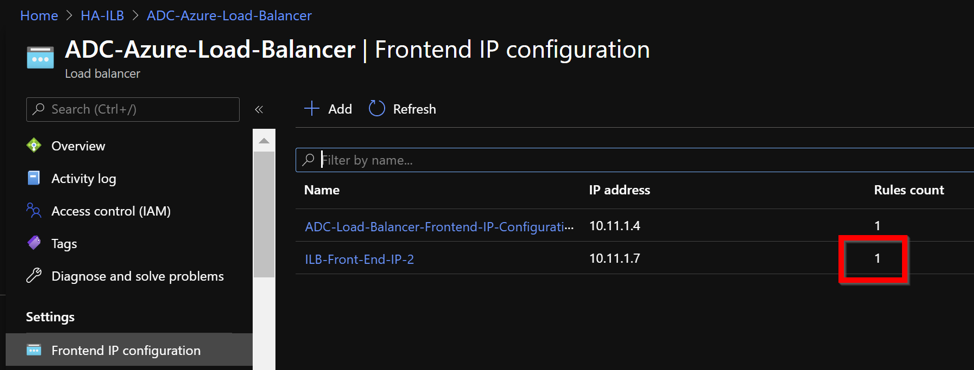
To find the private IP address of ADC Azure load balancer, navigate toAzure portal > ADC Azure Load Balancer > Frontend IP configuration.
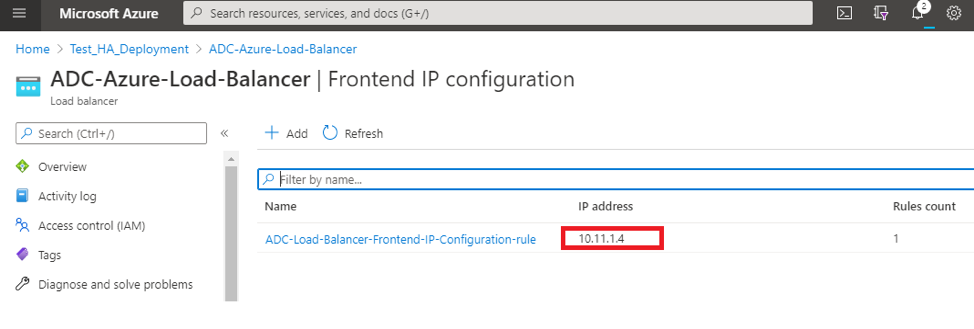
In theAzure Load Balancerconfiguration page, the ARM template deployment helps create the LB rule, back-end pools, and health probes.
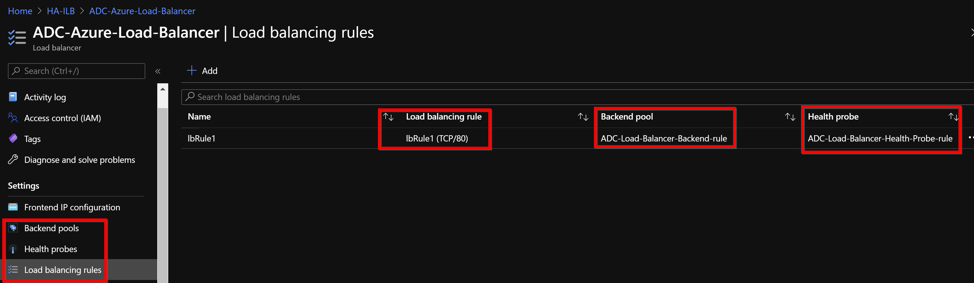
The LB Rule (LbRule1) uses port 80, by default.
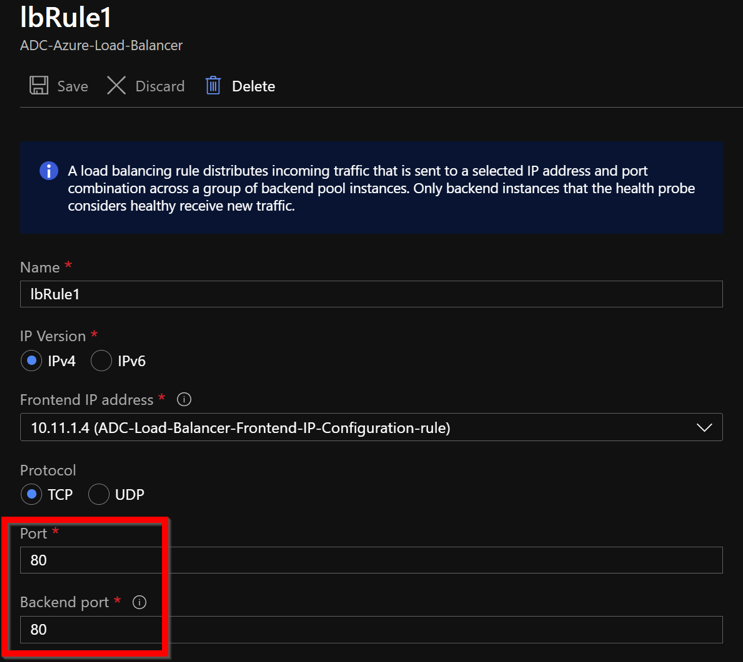
Edit the rule to use port 443, and save the changes.
Note
For enhanced security, Citrix recommends you to use SSL port 443 for LB virtual server or Gateway virtual server.
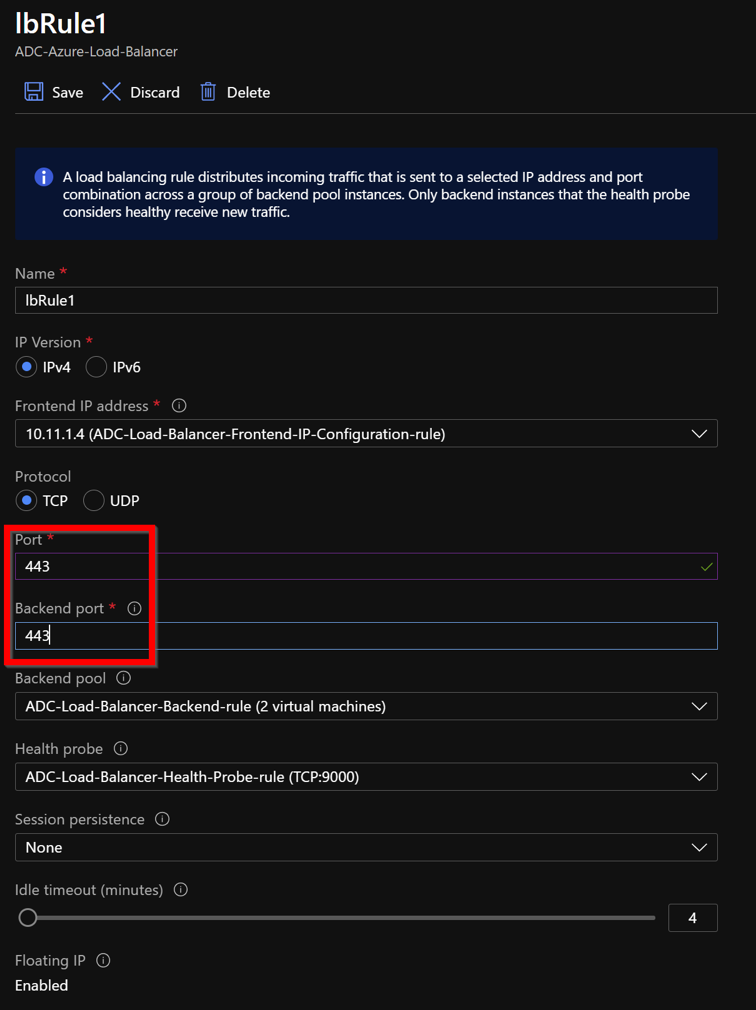
To add more VIP addresses on the ADC, perform the following steps:
Navigate toAzure Load Balancer > Frontend IP configuration, and clickAddto create a new internal load balancer IP address.
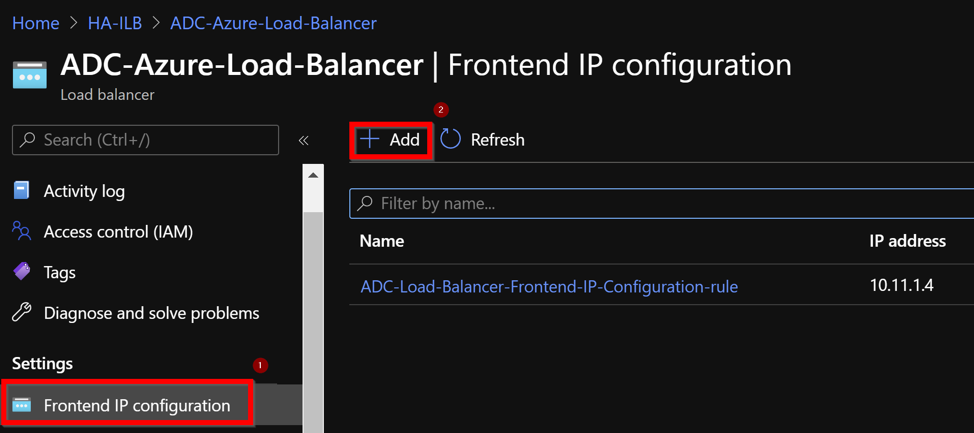
In theAdd frontend IP addresspage, enter a name, choose the client subnet, assign either dynamic or static IP address, and clickAdd.
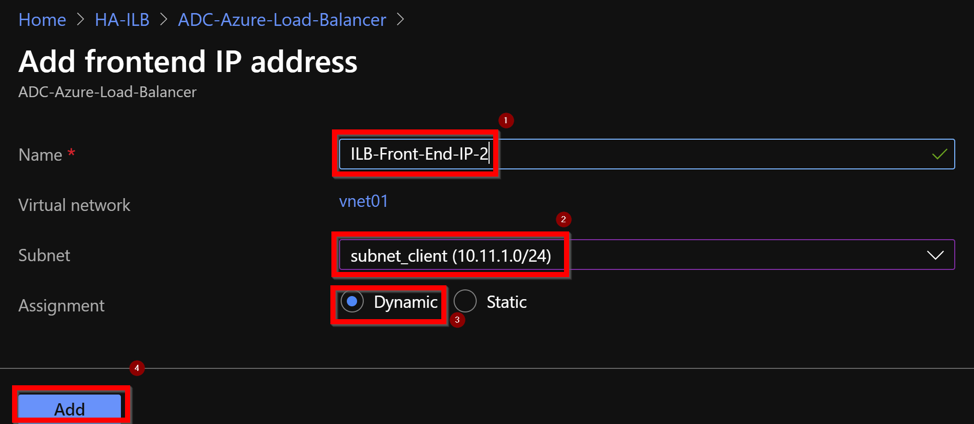
The front-end IP address is created but an LB Rule is not associated. Create a new load balancing rule, and associate it with the front-end IP address.
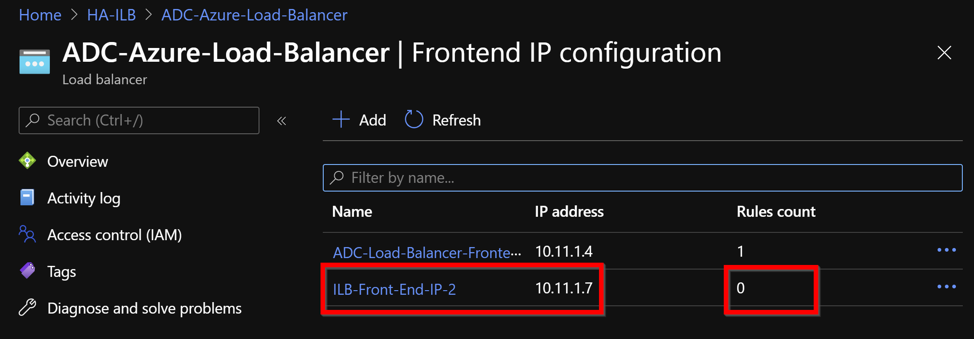
In theAzure Load Balancerpage, selectLoad balancing rules, and then clickAdd.
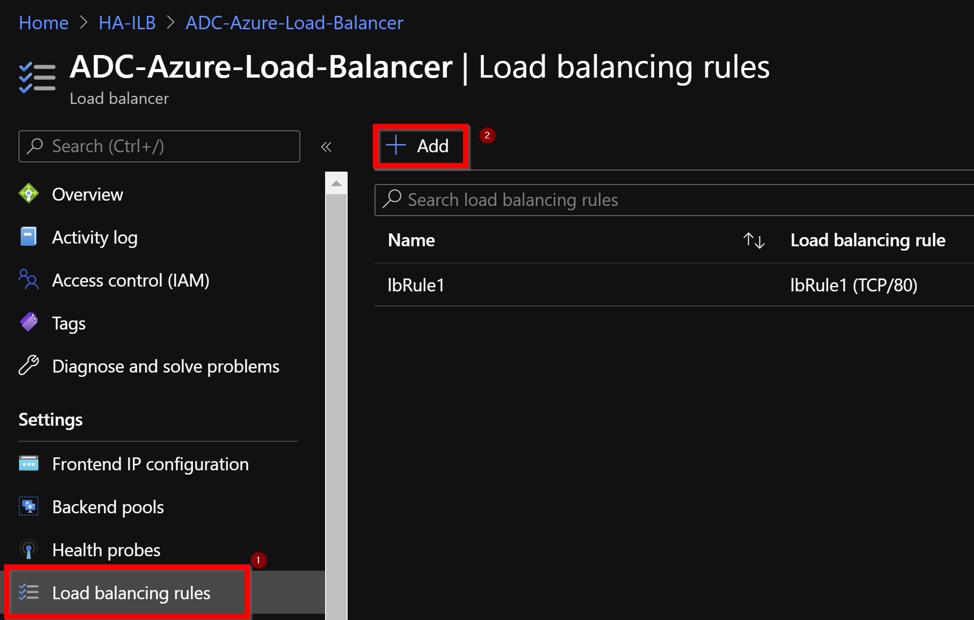
Create a new LB Rule by choosing the new front-end IP address and the port.Floating IPfield must be set toEnabled.
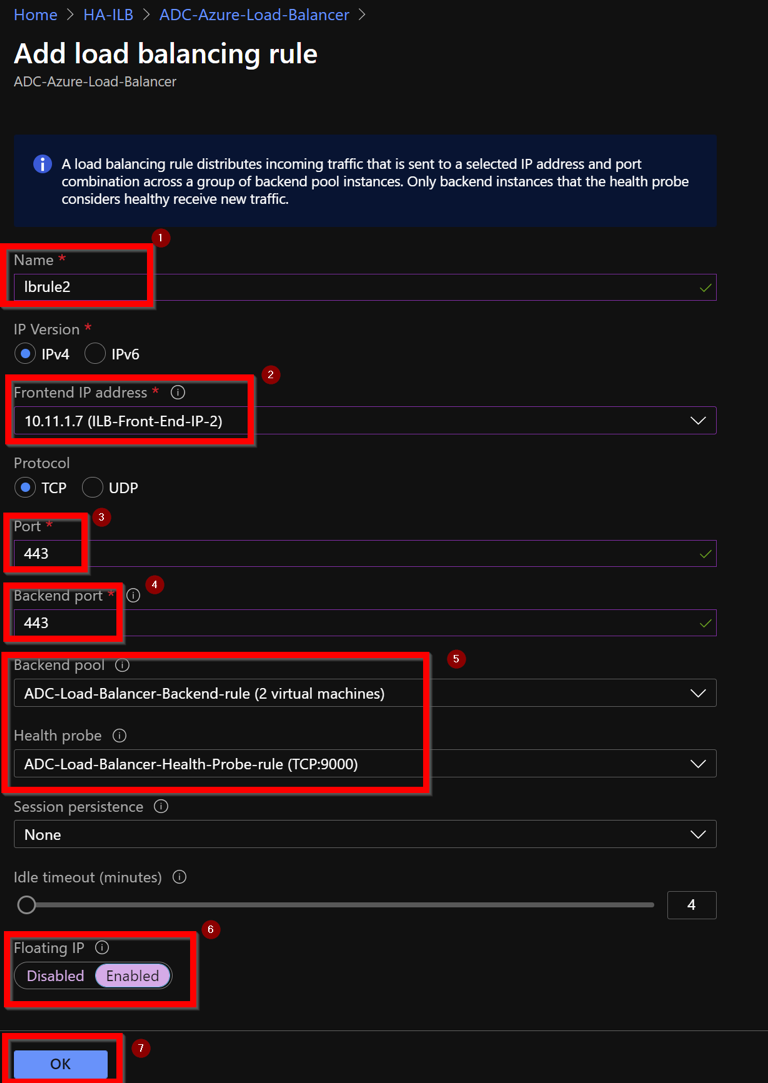
Now theFrontend IP configurationshows the LB rule that is applied.
Sample configuration
To configure a gateway VPN virtual server and load balancing virtual server, run the following commands on the primary node (ADC-VPX-0). The configuration auto synchronizes to the secondary node (ADC-VPX-1).
Gateway sample configuration
enable feature aaa LB SSL SSLVPN enable ns mode MBF add vpn vserver vpn_ssl SSL 10.11.1.4 443 add ssl certKey ckp -cert wild-cgwsanity.cer -key wild-cgwsanity.key bind ssl vserver vpn_ssl -certkeyName ckp Load balancing sample configuration
enable feature LB SSL enable ns mode MBF add lb vserver lb_vs1 SSL 10.11.1.7 443 bind ssl vserver lb_vs1 -certkeyName ckp You can now access the load balancing or VPN virtual server using the fully qualified domain name (FQDN) associated with the internal IP address of ILB.
See theResourcessection for more information about how to configure the load-balancing virtual server.
Resources:
The following links provide additional information related to HA deployment and virtual server configuration:
Related resources:
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select Do Not Agree to exit.
